Ultimate Guide to Controlled Unclassified Information (CUI)
Controlled Unclassified Information (CUI) is a critical element of every organization. From compliance regulations to brand reputation, understanding CUI and its protection requirements are likely at the top of your list for keeping data secure. Unfortunately, with the emergence of cyberattacks happening on an almost daily basis, it’s becoming increasingly important to arm yourself with resources in order to better understand how CUI works and what strategies can be implemented in order to effectively protect it from any potential risks. This guide lays out everything you need to know about identifying and protecting controlled unclassified information — from examples of what CUI is in Defense and Space to compliance requirements you can implement today.
This is your Ultimate Guide to Controlled Unclassified Information (CUI).
Introduction to Controlled Unclassified Information (CUI)
In the years following the 9/11 attacks, the Federal Government began to take steps to improve interagency information sharing, while establishing consistent and standardized handling safeguards. In 2010, Executive Order 13556 formally established the CUI Program in order to standardize the way the Executive branch handles unclassified information. Executive Order 13556 also named the National Archives and Records Administration (NARA) as the executive agent responsible for overseeing and leading the CUI Program’s implementation across the entire federal government.
In 2016, NARA issued a final rule amending 32 CFR Part 2002, which established a uniform policy for all Federal agencies and prescribed Government-wide program implementation standards, including designating, safeguarding, disseminating, marking, decontrolling, and disposing of CUI; self-inspection and oversight requirements, and other facets of the Program. This rule combined several markings such as For Official Use Only (FOUO), Law Enforcement Sensitive (LES), Sensitive but Unclassified (SBU), and Unclassified Controlled Technical Information (UCTI), bringing them under the umbrella term Controlled Unclassified Information (CUI).
What is the National Archives & Records Administrations (NARA) Role in CUI?
As the executive Agent for the Controlled Unclassified Information (CUI) program, the National Archives & Records Administration (NARA) is responsible for implementing the CUI program, which establishes a government-wide framework and policy that governs how CUI is managed, used, and shared.
NARA works with partners within the federal government to standardize practices across the executive branch by developing standards and procedures that ensure CUI is adequately protected. In addition, NARA serves as a central repository for the CUI Program and provides guidance to agencies on how CUI should be labeled, stored, and shared. NARA also works with industry and other stakeholders to ensure that CUI is adequately protected throughout its lifespan. With these efforts, NARA ensures that the federal government has access to the necessary tools and resources needed to protect CUI from unauthorized disclosure.
What is CUI?
Controlled Unclassified Information (CUI) is unclassified information that is marked or identified as requiring protection or dissemination controls pursuant to applicable laws, regulations, and government-wide policies. Simply put, Controlled Unclassified Information (CUI) is unclassified information that (a) the government creates or possesses or (b) a non-federal organization (government contractors, universities, etc.) creates or possesses in support of or on behalf of the government.
Public information, simple transactional information, and classified information are not considered CUI or FCI. For example, information posted on the United States Department of Defense’s website would not be considered CUI.
What is the Federal CUI Registry?
The Federal CUI Registry is a comprehensive resource created by the National Archives and Records Administration (NARA) to provide government agencies and other stakeholders (government contractors, universities, etc.) with an authoritative source on federal-level guidance regarding CUI policy and practices. The registry provides an authoritative source on what constitutes CUI, CUI categories, and CUI markings.
The Federal CUI Registry is an important tool for government agencies and organizations looking to ensure the protection of CUI. It enables them to better understand what types of sensitive data require special security protocols, as well as how best to protect it from unauthorized access or disclosure.
What are CUI Index Groupings & Categories?
Controlled Unclassified Information (CUI) is divided into index groupings and CUI categories, which represent a type of sensitive data that must be protected. Additionally, each CUI category also includes several subcategories that further specify the type of data contained within it.
Some examples of Index Groupings partially include international agreements, proprietary business information, and nuclear, defense, and export control.
Some examples of CUI Categories include Sensitive Personally Identifiable Information (PII), Controlled Technical Information (CTI), General Proprietary Business Information (PROPIN), Export-controlled Technical Data, Contractor Proprietary/Manufacturing Information, Intellectual Property, and Critical Program Information.
What are common CUI Categories in Defense & Space?
Common examples of CUI Categories that defense contractors must protect under DFARS/CMMC include:
Controlled Technical Information (CTI): Technical information with military or space application that is subject to controls on the access, use, reproduction, modification, performance, display, release, disclosure, or dissemination. Controlled technical information must be marked in accordance with the Department of Defense Instruction 5230.24, “Distribution Statements of Technical Documents”.
Export Controlled (EXPT): Unclassified information concerning certain items, commodities, technology, software, or other information whose export could reasonably be expected to adversely affect the United States’ national security and nonproliferation objectives. To include dual use items; items identified in export administration regulations, International Traffic in Arms Regulations (ITAR), and the munitions list; license applications, and sensitive nuclear technology information.
Geodetic Product Information (GEO): Related to imagery, imagery intelligence, or geospatial information.
Why is properly identifying CUI Important?
The task of identifying CUI is a shared responsibility among Federal Agencies & those Government Contractors with NIST 800-171 IT Compliance requirements. As a Government Contractor with NIST SP 800-171 requirements, being able to identify CUI is vitally important not only to the success of your CUI program, but also to your company’s bottom line.
Many organizations fall into the trap of misidentifying CUI, which causes them to over-mark or undermark the information as CUI. Overmarking information as CUI results in spending more resources, time, and money implementing and maintaining unnecessary cyber security requirements for their CUI Program. On the flip side, undermarking information as CUI not only puts an organization out of compliance with their contractual cyber security CUI requirements, but it can also cause serious reputational damage, as it leaves vital CUI data unprotected, increasing the risk of a data breach.
How can you Identify CUI?
As a government contractor with NIST 800-171 requirements, there are four main ways that you can identify CUI for your CUI Program.
First, any CUI that you receive from your federal customers should contain the proper CUI markings. This will let you know that you have received CUI.
Second, you can use the Federal CUI Registry and your federal customer’s CUI policies and procedures to identify information your creating that is CUI. Both of these resources should be used to identify the CUI that your organization is creating in the course of delivering your contractual responsibilities to your federal customer.
Third, any CUI that you will be handling while delivering services, products, or both to your federal customer, should be clearly identified by your contracting officer in your government contract. Unfortunately, this is rarely done by contracting officers and even the United States Department of Defense (DoD) has acknowledged that they need to do a better job regarding this.
Fourth, when in doubt, ask a Kraken Compliance CUI expert. Kraken Compliance’s team of federal IT compliance experts has more than 30 collective years of experience identifying, scoping, and protecting CUI.
What are Use Case Examples of CUI in Defense & Space?
Research and engineering data created by a defense contractor to test a robotic arm that will be used on army transport vehicles to lift supplies.
Research and engineering data created to test rockets, materials, space systems, etc., that will be used by the DoD.
Engineering designs of parts created to help the DoD launch or repair spacecrafts.
Geospatial information & imagery created for the DoD.
Who is responsible for marking CUI?
Federal agencies have had the long-standing responsibility to mark Controlled Unclassified Information (CUI), but in recent years, some of this responsibility has been shared with certain federal contractors. In particular, all DoD contractors and some federal contractors are contractually required to implement NIST 800-171 when handling CUI, which charges them with the responsibility of marking CUI on media. This responsibility can be traced to NIST 800-171 Security Requirement 3.8.4. Therefore, complete and effective protection of CUI data becomes a key responsibility of the contractor.
How to mark CUI?
Controlled Unclassified Information (CUI) can be found on a variety of media, including paper documents, solid-state storage devices, optical discs, magnetic disks, and magnetic tapes. It is important to clearly identify the media as CUI and who designated it as such in order to protect this sensitive information. Government contractors should use the NARA’s CUI Marking Handbook, NARA’s CUI Markings List, and Agency Marking Procedures and Policy Documents to assist with marking CUI.
Why CUI needs protecting?
Controlled Unclassified Information (CUI) is among our nation’s most sensitive type of information, second only to classified information. CUI is handled and created by government contractors at rapid rates; and can encompass next generation space capabilities, protected health information (PHI), information supporting warfighters, etc. CUI data breaches can therefore have devastating impacts to national security and government contractors.
How to Protect CUI?
What is NIST 800-171 ?
In an effort to help federal agencies safeguard Controlled Unclassified Information (CUI), the National Institute of Standards & Technology created NIST SP 800-171, which provides federal agencies with recommended security requirements for protecting the confidentiality of CUI. This publication documents a set of 110 security requirements across 14 families, designed to protect the confidentiality of CUI that is being handled by non-federal organizations and systems (‘non-federal organizations’ is just the government’s umbrella term for mostly private sector organizations).
The NIST 800-171 security requirements include the 15 basic safeguards from Federal Acquisition Regulation (FAR) and are used by all federal contractors to protect Federal Contract Information (FCI). The NIST 800-171 publication also provides a mapping of NIST 800-171 to other frameworks and standards, like the NIST 800-53 security controls.
Since NIST SP 800-171 was first published, many federal agencies have begun to require their contractors to implement these security requirements when handling CUI. The US Department of Defense (DoD) was the earliest adopter, who in 2016 began requiring all of its 320,000 defense contractors that handle CUI to protect this information by implementing NIST 800-171.
What is the Cybersecurity Maturity Model Certification (CMMC)?
The Cybersecurity Maturity Model Certification (CMMC) program was developed by the United States Department of Defense (DoD). The goal of this program is to strengthen the Defense Industrial Base (DIB) CUI & FCI protection programs, increasing assurance that DoD contractors have implemented their IT compliance requirements at the time of contract award.
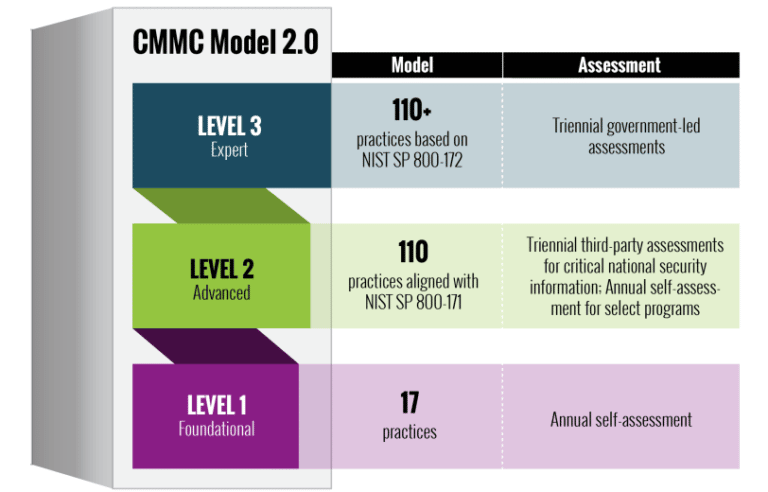
The CMMC 2.0 program matures the DoD’s current CUI cybersecurity requirements for contractors and subcontractors, by adding four key features:
-
Tiered Model: CMMC 2.0 moves away from a one size fits all approach for IT compliance and moves toward a risk based approach for protecting data. The CMMC program establishes a 3 tiered maturity model that progressively tailors in more advanced IT compliance requirements, depending on the type and sensitivity of the information that contractors handle. As a contractor handles more sensitive information, the DoD expects that the contractors will have implemented a more mature cybersecurity program to protect this information.
-
Security Requirements for CUI in critical programs: CMMC 2.0 establishes NIST 800-172 as the DoD’s security standard for protecting CUI for critical DoD programs & High-Value Assets (HVA). The DoD is still selecting the specific requirements and may include all or some of the requirements from NIST 800-172 in the CMMC Program.
-
Certification Assessment Requirement: CMMC 2.0 will require contractors to undergo certification assessments (designed to ensure compliance), based on the type and sensitivity of the information that the contractor handles.
-
Implementation through contracts: CMMC 2.0 requires contractors to achieve the CMMC certification level identified in their contracts as a condition of contract award. Contractors that do not achieve the CMMC certification level identified in their contracts by the time of contract award, will not be awarded the contract.
Frequently Asked Questions
The short answer is no. ITAR controls the export and import of defense-related articles and services on the United States Munitions List (USML) by establishing the criteria for what makes up ITAR data and import and export controls to protect the data. Only a subset of ITAR data is classified as Controlled Unclassified Information (CUI), which requires safeguarding with extra layers of protection to ensure U.S. national security remains intact and foreign policy objectives are met safely.
CMMC 2.0 is expected to be rolled out into DoD contracts in fiscal year 2023. The exact timing of the rollout is dependent on the federal government’s internal review process and rulemaking process.




